Cyber-Physical
Security
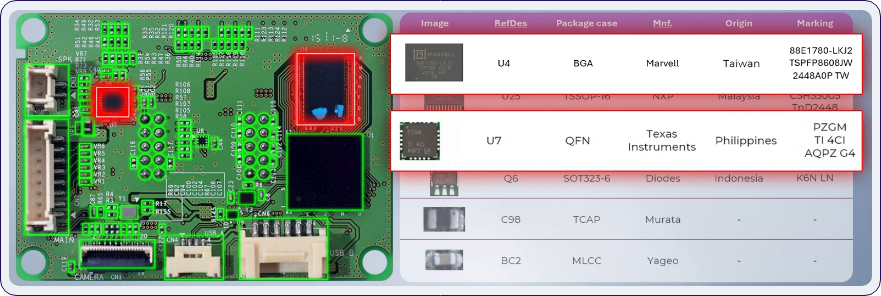
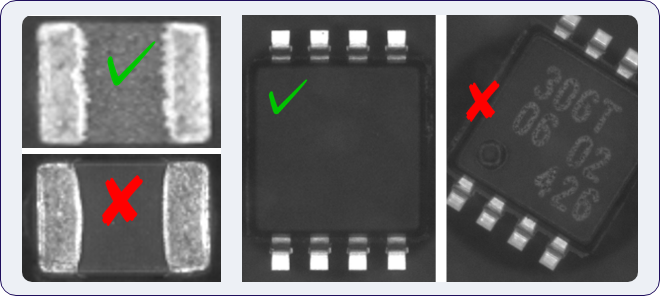
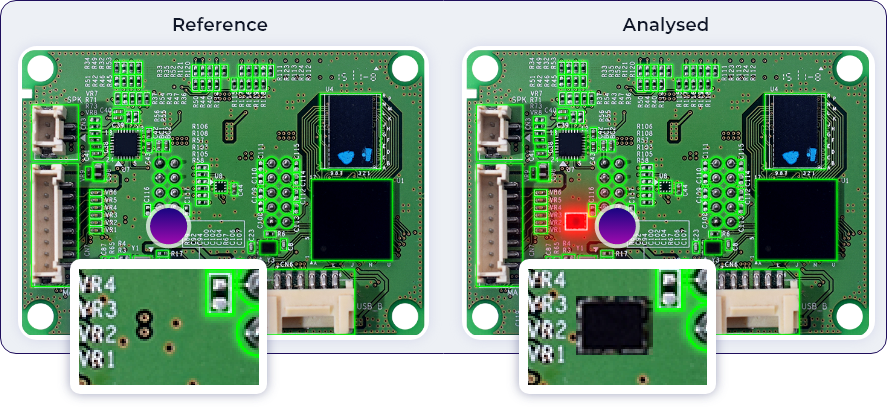
Unlike software-based cyberattacks, hardware tampering embeds malicious modifications into components during manufacturing or in the supply chain. These hidden threats can persist for years, bypassing security, leaking data, or disrupting systems.